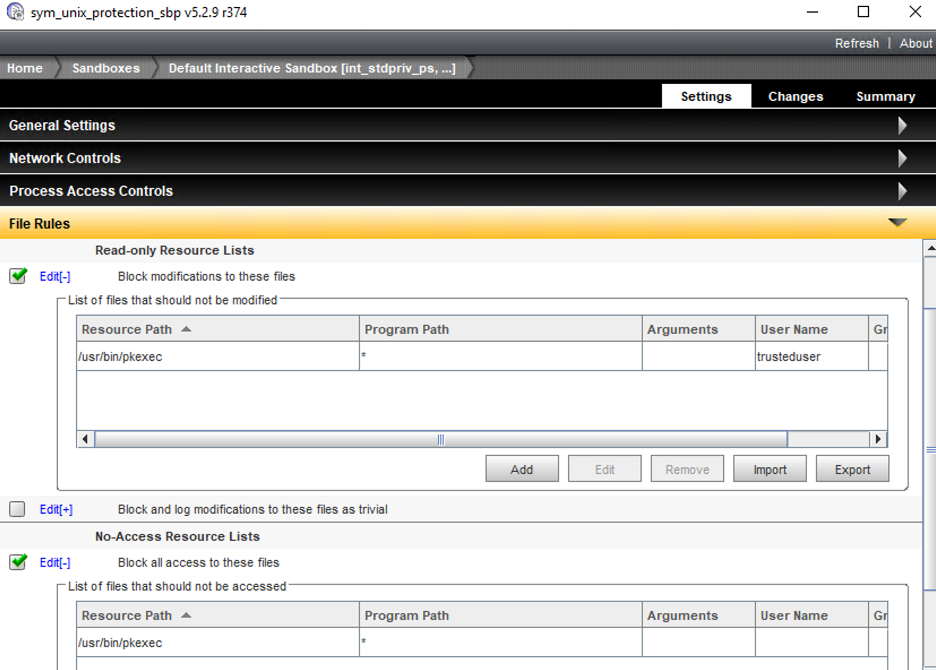
DCS protection for Polkit vulnerability CVE-2021-4034 aka PwnKit and authorized use of setuid programs
20409
23 March 2022
23 March 2022
- Prevent the launch of pkexec for all interactive users by adding the program to the No-Access File Resource List
- Configure exceptions to allow trusted users to be able to use the pkexec program. If your organization does not use the pkexec program, you can skip this step.